Trending about Internet


how to
How to Hack Almost Any Unprotected Webcam with Google


forum
Hi, My DEFY 600 UMS Oven Stopped Working.

forum
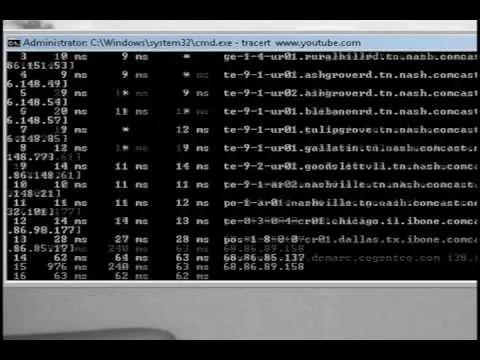
How to Pull a Ip Address
Featured On Gadget Hacks:
Gaming









Featured On Gadget Hacks:
iOS 18







Featured On Gadget Hacks:
Productivity & Shortcuts






forum
Wonderhowto
Featured On Gadget Hacks:
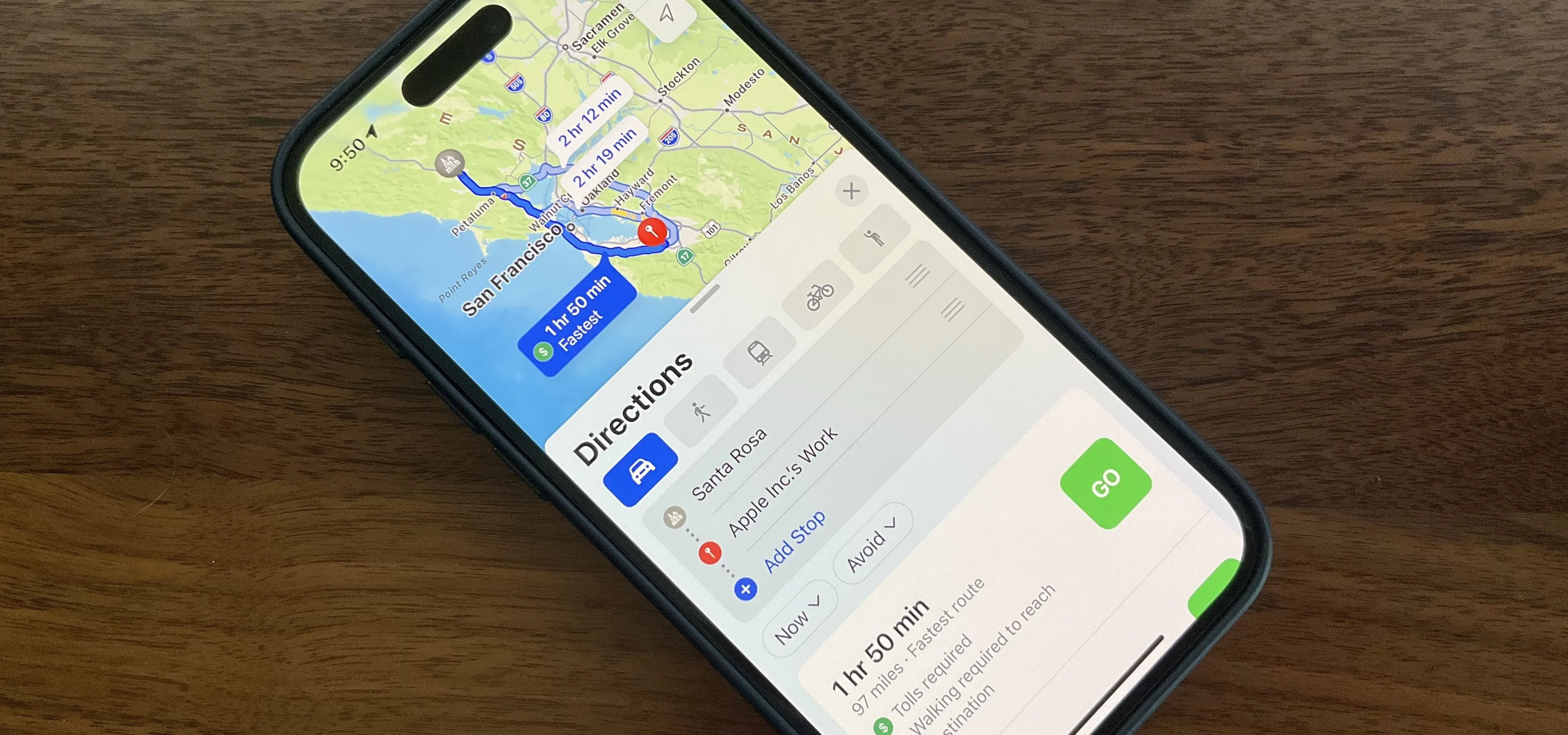
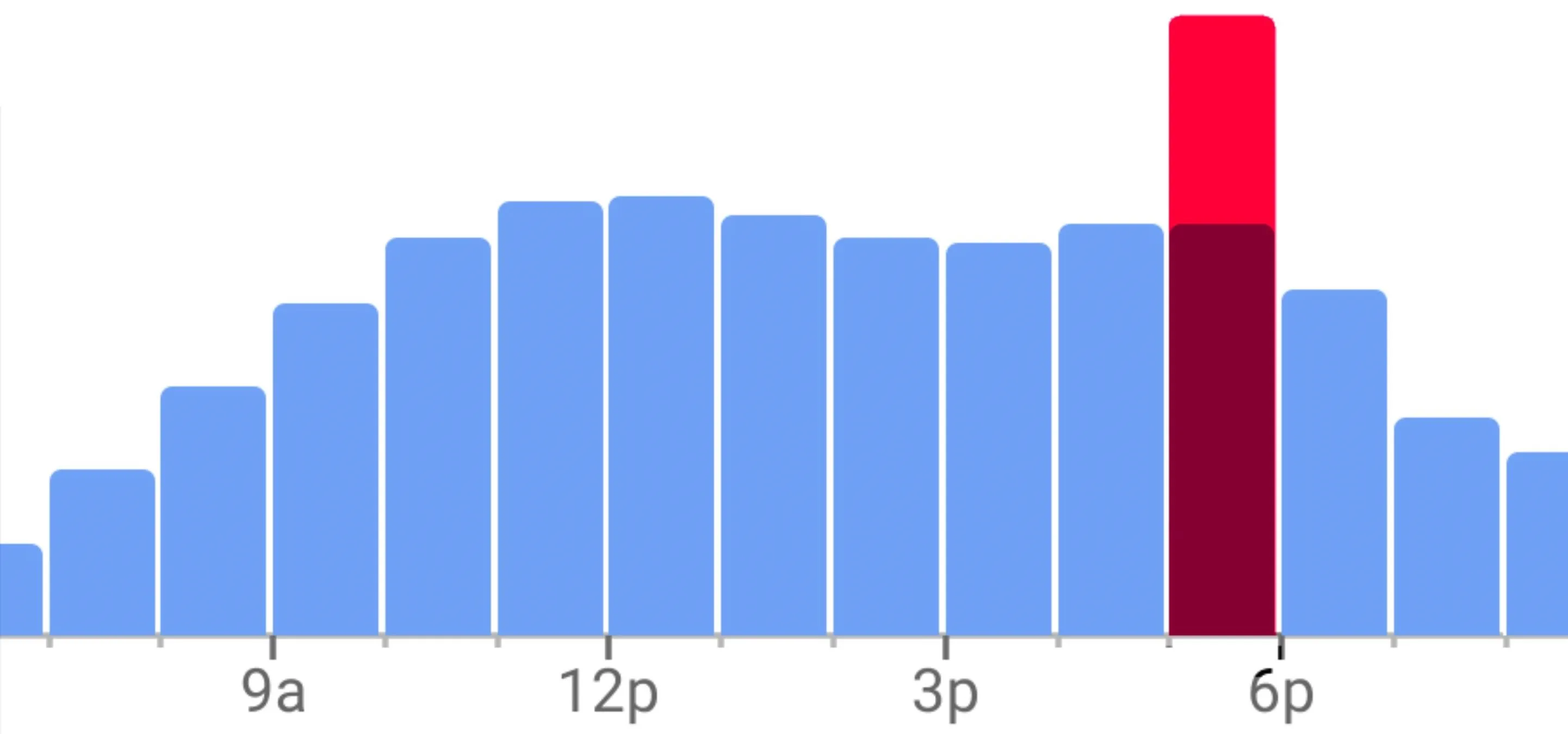
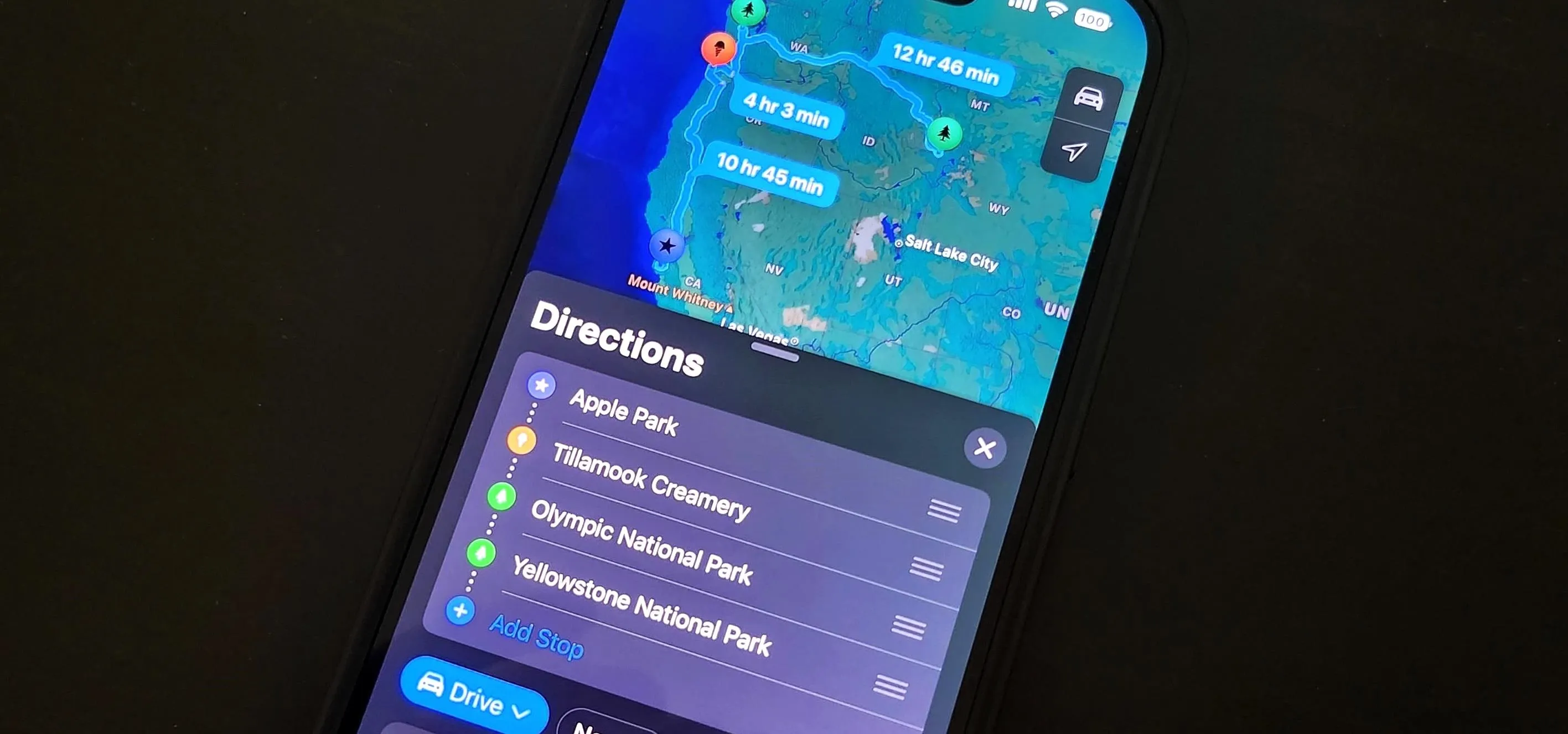
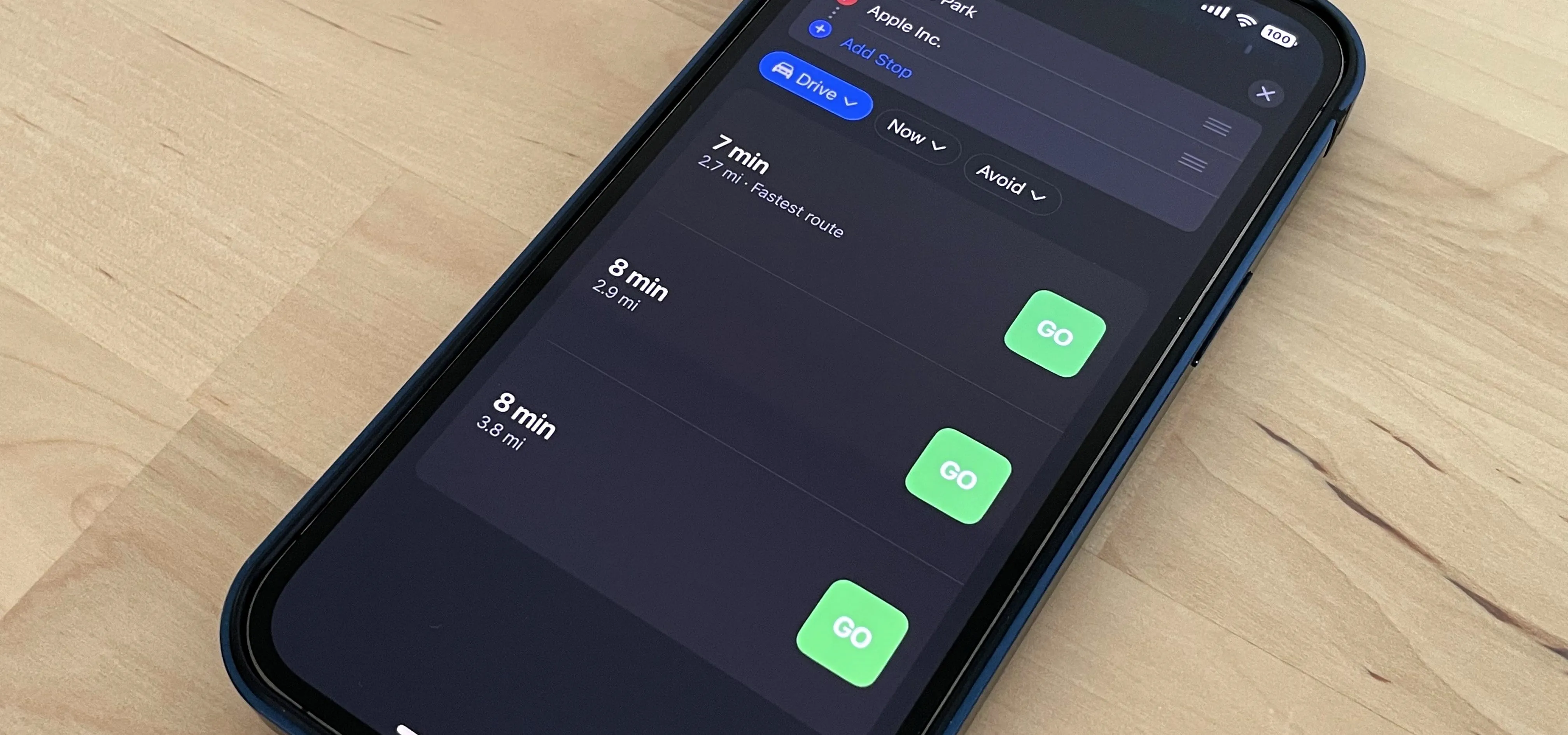
Travel Tips for Your Phone













forum
How to Make